In the rapidly evolving field of artificial intelligence (AI), securing AI models has become a critical concern. As AI development services continue to advance, it is essential to implement robust security measures to protect sensitive data and ensure the integrity of AI models. This article will outline several key techniques for securing AI models, safeguarding against potential vulnerabilities and threats.
- Data Encryption:
Data encryption is a fundamental technique for securing AI models. Encrypting both the training data and the model itself adds an extra layer of protection. Encryption algorithms such as Advanced Encryption Standard (AES) can be utilized to secure data during transmission and storage, preventing unauthorized access and tampering. - Access Control:
Implementing strict access controls is vital to limit access to AI models and related resources. Utilize strong authentication mechanisms, such as multi-factor authentication, to ensure that only authorized personnel can access the models. Role-based access control (RBAC) can be employed to assign specific permissions and privileges to individuals or groups based on their roles and responsibilities. - Model Validation and Sanitization:
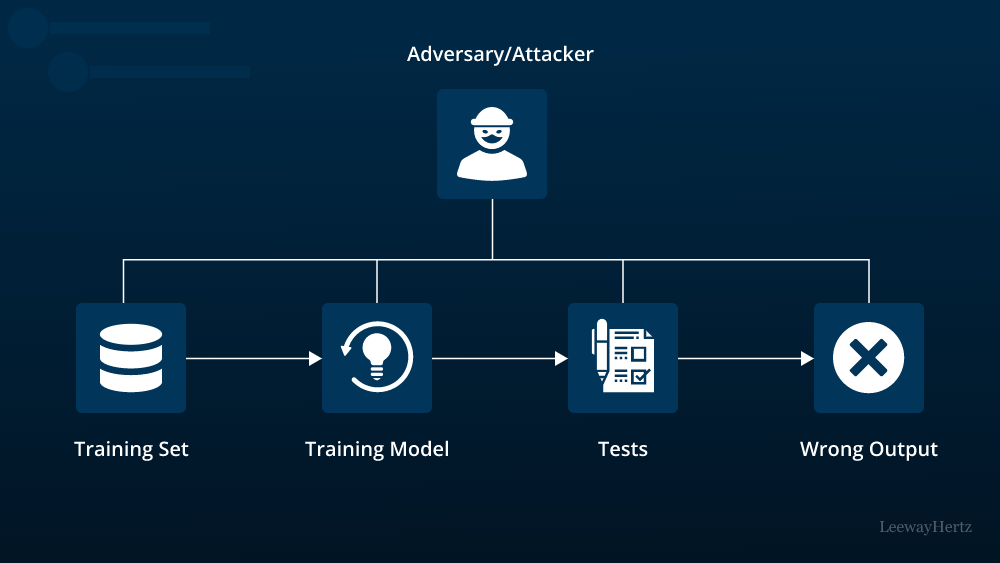
Thoroughly validating and sanitizing AI models is crucial to prevent potential vulnerabilities. Conduct rigorous testing and validation processes to identify and eliminate any weaknesses or flaws in the model. Utilize techniques such as input validation, parameter checking, and boundary testing to ensure the model behaves as expected and cannot be manipulated by malicious inputs. - Model Versioning and Tracking:
Maintaining a clear version history of AI models allows for effective tracking and monitoring of changes. By implementing version control systems, organizations can track modifications made to models, ensuring accountability and making it easier to identify any suspicious activities or unauthorized changes. This technique helps maintain the integrity of AI models and facilitates effective troubleshooting in case of issues. - Continuous Monitoring and Threat Detection:
Continuous monitoring of AI models is essential to detect any anomalies or potential threats. Implement mechanisms to monitor the model’s behavior, input-output patterns, and resource usage. Leveraging techniques like anomaly detection, intrusion detection systems, and machine learning-based algorithms can help identify and mitigate security breaches or malicious activities promptly. - Privacy-Preserving Techniques:
Privacy is a significant concern when dealing with AI models that process sensitive or personal data. Techniques such as differential privacy can be employed to preserve data privacy during the training process. Federated learning, where models are trained on distributed data without data leaving the local devices, can also be utilized to protect data privacy. - Regular Updates and Patching:
Keeping AI models up to date with the latest security patches is crucial to address any vulnerabilities that may arise over time. Stay informed about security advisories and updates provided by AI framework developers or service providers. Timely patching ensures that known vulnerabilities are fixed and protects against potential threats. - Secure Deployment and Infrastructure:
Securing the deployment environment and underlying infrastructure is essential for AI model protection. Implement secure network configurations, firewalls, and intrusion prevention systems to safeguard against unauthorized access and attacks. Regular security audits and penetration testing can help identify and rectify any security weaknesses in the deployment infrastructure.
Conclusion:
As AI development services continue to advance, securing AI models becomes increasingly critical. By implementing robust security measures such as data encryption, access control, model validation, and continuous monitoring, organizations can safeguard their AI models against potential vulnerabilities and threats. Additionally, privacy-preserving techniques, regular updates, and secure deployment infrastructure contribute to overall model security. Emphasizing these techniques will help ensure the integrity and confidentiality of AI models, fostering trust and enabling their effective utilization in various domains.
To Learn More:- https://www.leewayhertz.com/ai-model-security/